- Download Ss7 Attack Download
- Download Ss7 Attack Simulator
- Ss7 Attack Download
- Ss7 Download For Pc
- Download Ss7 Hack Tool
SS7 HACK
Signaling System Number 7
Download Ss7 Attack Download
SS7 is a common channel signaling system used in international and local telephone networks.

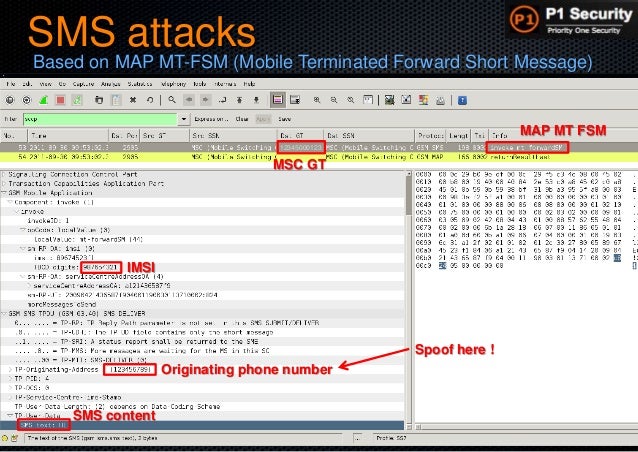
Note: In order to test SS7 attacks, you need to have an SS7 access or you can test in the virtual lab with the provided server sides of the attacks, the used values are provided. For brief intro on SigPloit and Telecom Architecture in general please click here. SigPloit is referenced in GSMA document FS.07 'SS7 and Sigtran Network Security'. Signalling System #7. Protocol suite used by most telecommunications network operators throughout the world to talk to each other. Standardized in the 1980s in ITU-T Q.700 series. When it was designed, there were only few telecoms operators, and they were either state controlled or really big corporations. Welcome To TomHat Today Going On How To Attack a SS7 Vulnerability On Kali Linux Download: git clone Buy This: https. SS7 attacks exploit the authentication capability of communication protocols running atop the SS7 protocol to eavesdrop on voice and text communications. According to telecommunications experts, all a cyber criminal would need to successfully launch an SS7 attack are a computer running Linux and the SS7 SDK – both free to download from the.
SS7 is a set of telephony signaling protocols that are used to set up most of the world’s public switched telephone network (PSTN) telephone calls. SS7 primarily sets up and tears down telephone calls, but other uses include number translation, prepaid billing mechanisms, local number portability, short message service (SMS), and a variety of mass-market services.
With access to SS7 and a victim’s phone number, an attacker can listen to a conversation, pinpoint a person’s location, intercept messages to gain access to mobile banking services, send a USSD (Unstructured Supplementary Service Data) command to a billable number, and conduct other attacks.
SS7 hacks are mobile cyber attacks that exploit security vulnerabilities in the SS7 protocol to compromise and intercept voice and SMS communications on a cellular network.
Similar to a Man In the Middle attack, SS7 attacks target mobile phone communications rather than wifi transmissions.
Two-factor authentication (also known as 2FA/OTP) via SMS using SS7 is inherently flawed as these SMS messages are unencrypted and can be intercepted.
With the code from the SMS in their hand, a cyber-criminal can potentially reset your password to Google, Facebook, WhatsApp account, or even your bank account.
Call Interception refers to actually intercepting live phone calls taking place on the Target phone, in real time as they happen.
Call Redirect refers to intercepting the phone call and forwarding it to your number in real time.
Being able to track the location of your target is a valuable goal for espionage operations.
The location tracking happens in real time even if the phone GPS is turned on or off.
@VPPOfficialGlobal mobile use has been on a major upswing for quite some time. From toddlers who learn to operate a mobile phone before they can even speak to professionals whose phones contain sensitive information. Mobile devices are now like opinions: everyone has at least one they hold very dear.
As 5G technology propagates and expands to reach new audiences and devices, the opportunities for mobile cyber attacks grow exponentially. While the YouTube browsing history of a toddler may be of little interest to hackers, anyone holding sensitive data or communicating privileged information is at risk. All thanks to legacy network protocols of global telecommunications.
The aging of legacy protocols with the evolution of hacking techniques create the perfect conditions to empower malicious activities on increasing crowded mobile networks. So it’s no wonder mobile malware attacks increased by 50% in 2019, and in 2020 are expected to continue to wreak mobile security havoc at an exponential rate.
Let’s meet one of the most prominent mobile network vulnerabilities threatening mobile service providers and users in the past years: SS7 loopholes.
Rather than target specific devices, sophisticated attacks are being perpetrated on entire networks. From a mobile service provider perspective, once your network’s SS7 protocol is successfully compromised, hackers are privy to your subscriber’s personal information. They can access text messages, phone calls, track device location, and all without your or the subscriber’s knowledge.
What is SS7?
Introduced and adopted in the mid 70s, SS7 (Common Channel Signaling System No. 7 or C7) has been the industry standard since, and hasn’t advanced much in decades. It’s outdated security concepts make it especially vulnerable to hackers.
SS7’s success has also, in a way, been its curse. At least when it comes to cyber security. The SS7 protocol is used everywhere, and is the leading protocol for connecting network communication worldwide. Because it is so prevalent, used by both intelligence agencies and mobile operators. From a surveillance perspective, it is considerably effective. As such, SS7 is an attacker’s best friend, enabling them access to the same surveillance capabilities held by law enforcement and intelligence agencies.
How does SS7 work?

The set of SS7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network to enable wireless cellular and wired connectivity. It is used to initiate most of the world’s public telephone calls over PSTN (Public Switched Telephone Network).
Over time other applications were integrated into SS7. This allowed for the introduction of new services like SMS, number translation, prepaid billing, call waiting/forwarding, conference calling, local number portability, and other mass-market services.
Components and elements that make up the SS7 Protocol Stack –
What are SS7 attacks?
SS7 attacks are mobile cyber attacks that exploit security vulnerabilities in the SS7 protocol to compromise and intercept voice and SMS communications on a cellular network. Similar to a Man In the Middle attack, SS7 attacks target mobile phone communications rather than wifi transmissions.
How do SS7 attacks work?
SS7 attacks exploit the authentication capability of communication protocols running atop the SS7 protocol to eavesdrop on voice and text communications. According to telecommunications experts, all a cyber criminal would need to successfully launch an SS7 attack are a computer running Linux and the SS7 SDK – both free to download from the Internet.

Once connected to an SS7 network, the hacker can target subscribers on the network while fooling the network into thinking the hacker device is actually an MSC/VLR node.
Download Ss7 Attack Simulator
What’s in it for the Hackers?
When a hacker successfully performs a MitM phishing attack, they gain access to the same amounts and types of information that are usually reserved for the use of security services. Having the ability to eavesdrop on calls and text messages, as well as device locations empowers hackers to gain valuable information.
A common security precaution used by many is one of the targets of SS7 attacks. Two-factor authentication (also known as 2FA) via SMS using SS7 is inherently flawed as these SMS messages are unencrypted and hackers know how to intercept them. With the code from the SMS in their hand, a cyber-criminal can potentially reset your password to Google, Facebook, WhatsApp account, or even your bank account.
The Risks to Digital Businesses
It doesn’t take an expert to see that it takes little skill and equipment for a hacker to successfully mount a man-in-the-middle MitM phishing attack. With most businesses managing their communications over cellular connections, it’s clear that SS7 attacks pose a significant risk. It’s important to remember that isn’t not only proprietary or confidential information hackers are interested in. The growing prevalence of IoT devices relyant on mobile networks to transmit data is expanding the risk playing field.
An enterprise’s IoT infrastructure, critical services can be prime targets. Such attacks can lead to potentially damaging breaches of confidential information as well as hijacking or disabling of mission-critical devices and services.
Considering how high the risks are, manufacturers are doing too little to warn businesses using IoT devices about potential security vulnerabilities in their products. This exposes network operators to attacks through compromised customer IoT devices on their network.
What can mobile operators do to prevent SS7 attacks?
The flaws and vulnerabilities inherent in the SS7 protocol are out of the jurisdiction of enterprises, small businesses as well as consumers. Being that, SS7 vulnerabilities cannot simply be removed or fixed.
The GSMA recommends that mobile network operations focus on consumer education. With consumers paying more attention to the security of their smartphones and IoT devices they are more likely to take action to secure their devices. Especially when it comes to critical applications and services like Smart Homes and Offices.
1. User Password Security
Two factor SMS authentication, flawed as it is, is still widely used. Security conscious businesses and services are gradually moving away from SMS and offer other methods of authenticating users which do not rely on antiquated telephone protocols like SS7.
Ss7 Attack Download
2. Monitoring & Event Analysis
If an SS7 network is successfully compromised, companies need to have the ability to monitor the activity during the attack. They need to be informed on security events in the context of what is happening on corporate servers as well as devices. This needs to be part of any enterprise mobile security strategy. Ultimately, businesses need to implement a defense that identifies threats and takes action before any damage occurs.
3. Regular Updates
Cyber security is not a set it and forget it deal even if you employ automation. Cybercriminals are always coming up with new exploits and approaches to compromise systems to get their hands on confidential data or hijack devices for ransom. Effective Patch Management is critical and complements adaptive defense. By employing real time analysis of endpoint security, business can ensure known vulnerabilities are sealed as soon as possible through software and firmware updates.
What can YOU do?
The only way to be fully safe from SS7 attacks is to simply shut your smartphone off. You and I both know that’s not an option. So what you can do is “know the enemy”. Being aware that malicious activities like SS7 attacks are prevalent and common is simply a necessity in 2020.
That said, with the billions of mobile phone users worldwide, the risk of you being targeted for surveillance by cyber-criminals is probably small. But if you happen to be a president, queen or even doctor holding sensitive patient information on their mobile, your chances are much higher than those of an average Joe. If you’re still using 2FA for banking services, you might very well be in danger of having your account compromised.
Considering just how easy it is to execute an SS7 attack and how much damage a successful one can do to both the victim and their service provider, one can only hope that innovation in telecom will protect us, the end users. For enterprises, government agencies and MSPs today there are numerous solutions ranging from complex customized mobile VPN systems, to innovative plug-and-play solutions.
Ss7 Download For Pc

Download Ss7 Hack Tool
If you want daily hacking tutorial and want to learn ethical hacking then Join our telegram channel and also we are sharing free udemy courses, so don't forget to join.
